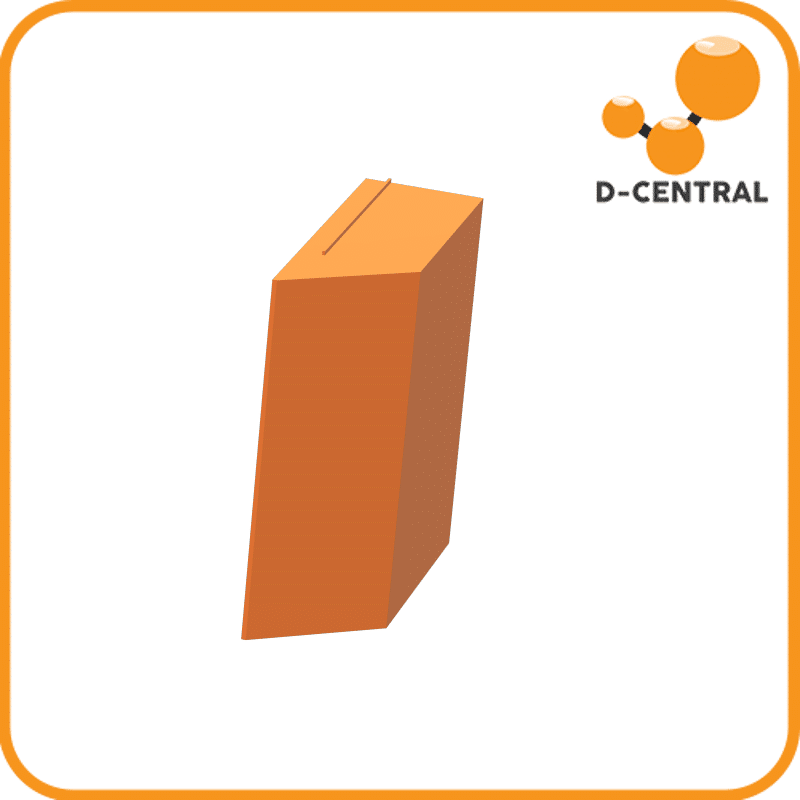
Hashboard Airflow Deflector for Antminer 19/21 Series
Our Hashboard Airflow Deflector is meticulously designed to optimize airflow and enhance the efficiency of your Antminer S19 and S21 enclosures. Crafted with precision, our deflectors are the perfect solution for managing heat dissipation and maintaining peak performance in your cryptocurrency mining rig. The Hashboard Airflow Deflectors will be perfect for those who want to transform commercial 19 and 21 series Antminers into a residential optimized rig, with one or two hashboards.
Key Features
- Optimized Airflow Management: Our Hashboard Airflow Deflectors ensure that your hashboard receives optimal cooling, significantly reducing the risk of overheating. By directing airflow precisely where it’s needed, these deflectors help in maintaining a stable operating temperature, which is crucial for efficient mining operations.
- Enhanced Efficiency: With our deflectors, experience reduced power consumption and improved hashboard performance. By preventing the escape of cooling air and focusing it on the hashboard, you can achieve lower power draw and higher mining efficiency.
- Screwless Installation: Our deflectors are ingeniously designed for a hassle-free installation. The screwless design means you can set up quickly without the need for additional fasteners. The convenient tab at the bottom ensures easy handling and quick removal, making maintenance a breeze.
- Perfect Fit for Antminer S19 and S21: Specifically tailored for Bitmain S19 and S21 enclosures, our deflectors address the suboptimal airflow caused by the considerable space on the sides of the stock enclosures. This ensures that every part of your hashboard is adequately cooled.
- Durable and Reliable: Made from high-quality materials, our airflow deflectors are built to last. They are robust and durable, providing long-term benefits for your mining setup.
Technical Specifications
- Material: High-quality, PETG
- Compatibility: Antminer S19 and S21 series
- Installation: Screwless, with easy-to-use bottom tab
Benefits
- Improved Mining Efficiency: By optimizing the airflow, our deflectors help in reducing power consumption, leading to cost savings and improved mining profitability.
- Extended Hardware Lifespan: Effective cooling ensures that your hashboard components do not overheat, thereby extending their lifespan and maintaining their performance over time.
- Enhanced Performance: Experience better hash rates and stable mining operations with consistent cooling provided by our airflow deflectors.
Printed and delivered by D-Central Technologies, a trusted name in the cryptocurrency mining industry, our Hashboard Airflow Deflectors are an essential upgrade for serious miners.
Explore the future of efficient mining with our Hashboard Airflow Deflectors and take your mining operations to the next level.
Designed by johnny9dev, licensed under the Creative Commons – Attribution – Share Alike license.
| Weight | 360 g |
|---|---|
| Dimensions | 8 × 25 × 22 cm |
You must be logged in to post a review.











Reviews
There are no reviews yet.